VERTU IRONFLIP: A Perfect Fusion of Intuitive Design and Heroic Colours
VERTU IRONFLIP, a folding screen mobile phone for high-end men, not only has the top technological configuration, but also the
Introduction
At the beginning of the 19th century, Mayer Rothschild’s five sons, starting from Frankfurt, expanded their business to London, Paris, Vienna, and Naples. They established an information network, using carrier pigeons, couriers, and chartered ships to transmit information throughout Europe, faster than anyone else. Through this network, the Rothschild family was able to obtain news and information faster than anyone else and profit from it in arbitrage and business deals. It is well known that this also allowed Nathan Rothschild to learn about Napoleon’s defeat at Waterloo 36 hours earlier than the official messenger in London.
In all markets, information is valuable. People are competing fiercely to have priority access to information. Even today, in traditional markets, high-frequency trading institutions and hedge funds spend tens of billions of dollars on towers and cables around the world in an arms race to gain an information advantage measured only in milliseconds.
The encrypted world is no exception. On the chain, the competition for priority access to order flow and order rights is intensifying. The concept of “maximum extractable value” (MEV) has moved from a niche topic to the forefront of almost all encrypted protocols. We see more and more discussions in the community about the impact of MEV on the transparency, sustainability, decentralization, security, censorship resistance, and valuation of protocols.
In this report, we will discuss several key issues surrounding MEV. We first introduce what MEV is and why it is important. Then, we explain why we think MEV is fundamental and how to weigh it. We also summarize the current state of MEV and some of the main players in this field. Finally, we discuss future trends and some open issues.
Key Points:
– Understanding MEV is important as it affects security, stability, and user experience. It is also a key component of blockchain token appreciation and impacts two fundamental attributes of blockchain networks: decentralization and censorship resistance.
– MEV is foundational. While there are solutions to mitigate certain forms of MEV, a certain amount of MEV will always exist. Blockchain networks, as smart contract platforms, have the inherent advantages of being unrestricted and permissionless, but they are also cursed by MEV. Protocols and applications need to carefully consider trade-offs when dealing with MEV.
– We estimate that on PoW Ethereum, MEV has contributed at least 8% of miners’ total revenue since 2020. Capturing MEV opportunities in major categories – arbitrage, liquidations, and sandwich attacks – is extremely competitive and dominated by a few searchers.
– Although cross-chain MEV currently has negligible influence, it could become a highly centralized force affecting the development of all blockchains. MEV is also an increasing threat to the stability of blockchain networks in the long run.
– We can envision scenarios in the future where a certain amount of MEV is returned to users through payment for order flow (PFOF) or transaction flow auctions. The most likely path in these scenarios is a greater degree of centralization of block builders and a reduction in the yield of validators, but more research is needed to achieve these goals.
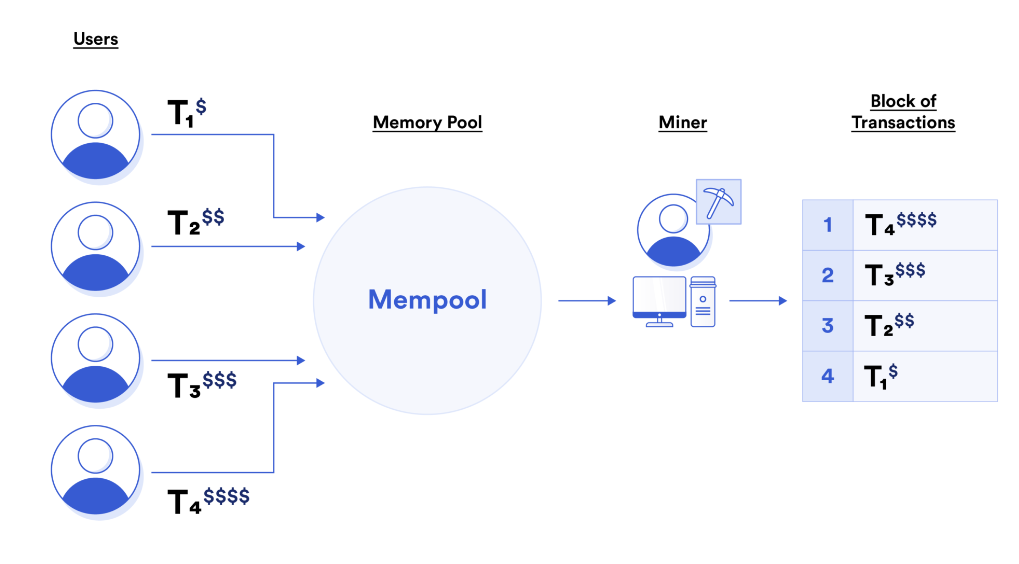
Memory Pool:
– MEV was first defined in a groundbreaking report by Daian et al. The researchers identified and studied multiple bots on Ethereum that compete for priority ordering and detailed their impact on the blockchain. The paper also first proposed the definition of MEV, which is “the total amount of value that miners on Ethereum can extract from transaction ordering over a given time frame, which may include the value of transactions in multiple blocks.”
Ethereum Transaction Lifecycle:
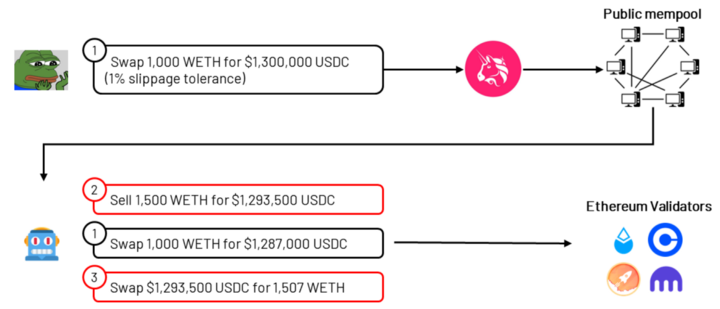
– Assuming Joe wants to exchange 100 ETH for USDC on a decentralized exchange, he navigates to the Uniswap frontend and connects his MetaMask wallet. He specifies the transaction inputs: 1000 ETH for $1.3 million USDC, a slippage tolerance of 1.0%, and signs the transaction.
– His transaction is first sent through MetaMask’s default RPC endpoint to Infura. Infura propagates this request to other nodes in the Ethereum network, which then propagate it to their connected nodes in a similar manner.
– Each validator has its own memory pool, which is a database of pending transactions maintained by each validator. It builds a block of transactions based on its own memory pool. Typically, these transactions are ordered by Gas fees. Alternatively, validators can run custom software to order transactions according to their own rules and logic.
– Every 12 seconds, an Ethereum validator is randomly selected to build and propose a block of transactions. The proposer broadcasts the creation of the new block to the network. A committee of other validators is randomly selected to determine the validity of the block and to attest to it. Once transactions are included, they are removed from the node’s memory pool.
How MEV is Generated:
– Everyone can view the memory pool. Since Joe’s transaction is publicly submitted, it creates several potential profit opportunities:
– Sandwich: Joe’s ETH to USDC transaction has an unusually large slippage tolerance of 1%. While he hopes to get $1.3 million, he signals to the world that he would accept $1.287 million. Other entities monitoring the memory pool can see Joe’s willingness and attempt a “sandwich attack,” giving Joe the worst execution price to obtain a risk-free profit. They sell ETH before Joe (front-running his transaction), allowing Joe to sell at the minimum limit he defined, and then repurchase ETH at a relatively cheaper price to make a profit.
– Arbitrage: After Joe’s transaction, there will be a temporary price discrepancy between the ETH-USDC trading pair on Uniswap and other DEXs. Bots constantly look for these discrepancies and will automatically execute arbitrage (back-running Joe’s transaction) after Joe’s transaction to obtain a risk-free profit.
Privileged validators are more likely to capture this profit. Ethereum’s consensus protocol only enforces the protocol at the block level, allowing validators to choose the transactions that occur within each block. Therefore, validators can decide which transactions to include and the order in which they are executed.
For example, assume there is $100 of arbitrage profit available through a dex. Alice can submit a transaction to try to capture the profit, paying a $1 transaction fee. However, the memory pool is visible to everyone. Bob sees Alice’s transaction in the memory pool, copies her transaction, and offers to pay a $2 fee. Others may follow suit.
If left unregulated, users will be dynamically incentivized to create off-chain agreements with validators/miners to ensure their transactions are included or can be ordered. Alternatively, validators/miners themselves can submit and prioritize their own transactions to capture all $100 of the arbitrage profit

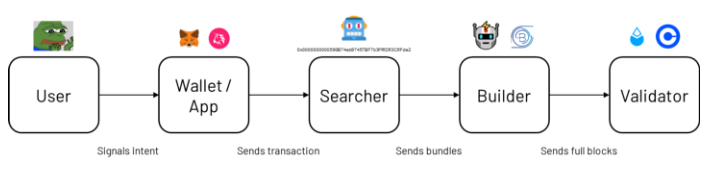
Users: Anyone who wants to express and submit ideas to change the state of the blockchain.
Wallet/Application: The user interface that transforms users’ ideas into blockchain transactions.
Searchers: Entities that monitor the memory pool and submit transactions to extract MEV.
Builders: Aggregate transactions from various sources to create a complete block, ideally one that maximizes returns.
Validators: Fulfill consensus duties, such as proposing and proving blocks.
The latest definition of MEV in PoS blockchains is: the total value that validators can extract across blocks (or a series of blocks) given a certain environmental state and all available operations. Validators are generally unable to change the state of their environment, including blockchain rules, smart contract code on the blockchain, the set of transactions in their memory pool, etc. Executable operations include reordering, censoring, and inserting transactions. They can also join more niche strategies, such as changing block timestamps, manipulating “randomness,” executing other validators, and so on.
The three largest and most competitive MEV revenue pools are arbitrage, liquidations, and sandwich attacks.
Arbitrage: Arbitrage is the largest source of MEV revenue. Arbitrage is considered MEV because ordering is important here. Arbitrage transactions occur in all markets. Traders in traditional markets face some inventory or timing risks, but many MEV transactions can be automated: either all the transactions that want to be made can proceed smoothly, easily obtaining risk-free profits, or all transactions fail. Atomic arbitrage allows searchers to operate with minimal capital on hand in some cases. However, there are also classic statistical arbitrage transactions with inventory and timing risks, such as price arbitrage between CEX and DEX.
Competition in atomic arbitrage is fierce. Arbitrage requires:
1. Running optimized hardware and software to quickly find opportunities in thousands of token pairs.
2. Submitting extremely efficient transactions to minimize Gas fees. The second phenomenon is known as “Gas golfing,” which allows MEV searchers to bid on transactions.
Liquidations: Money markets like Aave, Compound, and Maker allow users to deposit some assets as collateral and borrow other assets. As the value of the collateral assets fluctuates, so does the user’s borrowing power. If the borrower exceeds the budget limit, these protocols rely on market participants to liquidate the borrower, but at a cost. To incentivize liquidation, the protocol charges a liquidation fee to the borrower and gives a portion of the fee to the liquidator. This is where the opportunity for MEV lies. Searchers compete to monitor the positions of all borrowers and try to be the first to liquidate the position, thus collecting the liquidation fee for themselves. Similar to arbitrage, liquidation events are highly competitive. During periods of sharp market downturns, the competition to liquidate borrowers leads to huge Gas fees. Similarly, searchers who can optimize their code are the most competitive and can bid on liquidations.
Sandwich Attacks: Transactions on the blockchain do not happen immediately. When users send Swap transactions, they define an acceptable percentage change in price (“slippage”) that may occur while the submitted transaction is pending. If users set too high a slippage for their transactions, a “sandwich attack” occurs. Searchers exploit these errors by frontrunning the user’s transaction to the highest acceptable slippage, causing the transaction to occur at a disadvantageous price. Then they execute the user’s transaction, further moving the price. After that, the searcher backruns the transaction, netting a profit. For example, suppose the searcher pays 4 ETH in Gas and priority fees, and their risk-free profit is 3 ETH.
The provided text is a comprehensive analysis of the concept of Miner Extractable Value (MEV) in the context of blockchain and cryptocurrency, particularly focusing on Ethereum. The text discusses various aspects of MEV, including its impact on network security, stability, user experience, and the economy of the blockchain. It also explores different strategies and mechanisms to manage and capture MEV, as well as the potential future growth of MEV opportunities.
The text begins with an illustrative example of a user attempting to exchange 1000 WETH for USDC with a 1% slippage tolerance. It explains how a search engine, upon detecting the transaction in the public mempool, creates a frontrunning and sandwich attack transaction package and sends it to a validator via an MEV bot.
The text then delves into the concept of sandwich attacks, which rely heavily on transaction ordering privileges. It highlights the risks faced by searchers if any part of the sandwich attack fails to execute, leading to potential losses.
The article also discusses the negative perception of sandwich attacks within the crypto community, describing them as a form of malicious MEV that is largely seen as pure value extraction. It mentions that some searchers publicly declare their refusal to engage in sandwich attacks to avoid criticism and backlash.
The text further explores various long-tail MEV opportunities, such as Apecoin airdrops, accidental mispricing of NFTs, and遗留 (leftover) tokens in smart contracts like 1inch. These opportunities can be exploited by MEV bots to generate significant profits.
The importance of understanding MEV is emphasized, as it affects the fundamental attributes of blockchain networks, including decentralization and censorship resistance. The text also discusses the negative externalities associated with MEV, such as network congestion, high and volatile transaction fees, and the waste of block space due to failed bids.
The article highlights the potential for MEV to disrupt network stability, as high MEV rewards can incentivize validators and miners to engage in malicious activities, such as reorg attempts. It also mentions the threat of spam transactions leading to fee market failure, as seen in the Solana network’s downtime earlier this year.
The text also examines the centralizing force of MEV, as block producers can extract MEV by either capturing it themselves or selling the right to reorder transactions to others. It discusses the potential for vertical integration and horizontal consolidation in the MEV market, leading to increased dominance by professional validators and searchers.
The article also explores the role of MEV in enhancing economic security, as MEV income can increase the security budget of a blockchain. However, it also acknowledges that certain types of MEV can degrade user experience, leading to users abandoning the network and reducing fees and economic security.
The text suggests that a well-designed blockchain should democratize MEV extraction and facilitate easy entry for new players to promote competition and prevent oligopolies. It also highlights the potential for MEV to reduce user costs, maintain algorithmic stability, and enable unique DeFi designs.
The article discusses the long-term value of L1/L2 tokens, which lies in monetary premium and/or MEV. It emphasizes the need for platforms to carefully consider how to create and capture MEV to prevent it from leaking to other entities.
The text provides examples of how current protocols capture and internalize MEV, such as Optimism’s MEV auctions, Aurora’s management of MEV order flow, Osmosis’s efforts to minimize and capture MEV, and Cosmos’s proposal to create a cross-chain block space market.
The article predicts that MEV will increase exponentially over the next decade due to the growth of complexity, new protocols, and the emergence of new asset classes like NFTs. It also highlights the inherent presence of MEV in blockchain networks that allow anyone to deploy smart contracts and transfer value.
The text proposes a framework for understanding MEV dynamics by breaking down blockchains into three fundamental components: the virtual machine, the consensus mechanism, and the block space market. It discusses the trade-offs and considerations for each component in relation to MEV.
The article concludes by examining the current state of MEV, particularly in the context of Ethereum. It discusses the role of Flashbots in shaping the MEV landscape and the challenges posed by recent sanctions on Tornado Cash. The text also explores the origins of Flashbots, its efforts to mitigate the negative externalities of MEV, and the introduction of MEV-geth, which created an off-chain private transaction pool and a sealed block space auction.
In summary, the text provides an in-depth analysis of MEV in the blockchain ecosystem, discussing its implications, management strategies, and potential future developments. It emphasizes the need for a balanced approach to harnessing MEV opportunities while minimizing its negative impacts on network stability, user experience, and decentralization.
In fact, only three relayers, accounting for 12.5% of the mev-boost market share, do not censor transactions. Why has this issue suddenly attracted attention? When Ethereum adopted PoW, censorship issues were not common because mining pools were their own block builders. Even if the lightning robot tried to censor transactions, these miners could append the censored transactions after the lightning robot’s bundle.
Assuming there is a price difference between Uniswap on L1 Ethereum and Uniswap on Arbitrum. ETH is priced at $1400 on Ethereum and $1300 on Arbitrum. How to arbitrage? Official bridge: Buy 1 ETH on Arbitrum and use Arbitrum’s official bridge to move ETH to L1 Ethereum, which takes 8 days. Hope that the price will not fluctuate too much by then (or use perpetual futures to hedge). Then sell on L1 Ethereum. Third-party bridge: Use a third-party bridge to move ETH to L1 Ethereum. It takes 5-20 minutes, depending on the user’s priorities for speed, security, and revenue. CEX: Some firms directly accept deposits from Arbitrum. The time from deposit to withdrawal is variable, but it is roughly between 5-20 minutes. Proprietary balance sheet: Hold a combination of ETH and USDC on both chains and arbitrage between the two chains when opportunities arise. Rebalance from time to time to ensure that there is sufficient inventory on both chains. Obviously, alternative 4 can almost always make you profitable. But this strategy is also the most capital-intensive option, benefiting professional market makers and institutions. In fact, this dynamic stimulates collusion across multiple chains. Cross-chain MEV execution is a probabilistic event, and an institution can set up validators on multiple chains to minimize risk and capture MEV more effectively.
Multi-block MEV was not feasible on Ethereum before due to power limitations, as no one knew in advance who the next proposer would be. However, after the merge, anyone knows who will propose the next 32 blocks within an Epoch. There are currently more than 445,000 active validators, and it seems unlikely that a validator will be selected to propose multiple blocks in an Epoch, let alone consecutive blocks. However, multiple validators are often under the same entity or pool. Bitcoin Base alone controls 13% of active validators, giving them about a 39% chance of proposing at least two consecutive blocks. Perhaps the biggest threat posed by multi-block MEV is manipulating the TWAP price oracle to exploit money market protocols. While this is not the main threat, the risk of these attacks increases when TVL returns. But this is just a possibility, and we have not yet seen multi-block MEV with such motivation, especially for several consecutive blocks. Five consecutive blocks mean that an entity can control an entire minute of block production on Ethereum.
User intent and transaction flow are major sources of MEV. Therefore, we can imagine a scenario where wallets or applications auction their transaction flow to builders. Wallets, applications, and infrastructure providers are in a favorable position to benefit from aggregating and auctioning order flow, thus generating revenue.
The outlook seems very bleak – the market structure of cryptocurrencies is tending towards traditional finance: transactions enter black boxes, managed by privileged intermediaries, and the results are displayed from the other end. Fortunately, we see more and more people getting involved in MEV, from discussing what is fair, researching appropriate market design, to actually implementing solutions to mitigate EV throughout the entire supply chain.
This is a long report, and we have only touched the surface of MEV. Therefore, we have listed some references below for readers who are interested in delving into certain topics:
Flash Boys 2.0 — Daian et al.: Seminal report investigating MEV and its impact on Ethereum. Ethereum is a Dark Forest — Paradigm: Riveting first-hand account of avoiding generalized frontrunners on Ethereum. Ethereum Blockspace — Who Gets What and Why — Paradigm: First principles based approach to understanding blockspace markets and MEV. MEV … wat do? — Phil Daian: Arguing why MEV is fundamental and how to manage MEV. MEV Manifesto — Delphi Digital: Deep dive into MEV design and solutions on Ethereum. Optimism’s MEVA Proposal: Optimism’s original proposal of MEV auctions on L2. MEVA (What is it good for?) — Ed Felten: Argument for why MEV Auctions are harmful to user experience and makes centralization worse. Formalization of Cross-Domain MEV — Obadia et al.: Investigation and formalization of cross-domain MEV.